WannaCry — Do you feel lucky?

Was it just ransomware?
During the hysteria around the WannaCry ransomware outbreak, a thought struck me:
Ponder this: for all the critical orgs with noisy ransomware, how many have been hit by quiet malware playing the long game...? #WannaCry
— Josh Grossman 👻 (tghosth) (@JoshCGrossman) May 14, 2017
A bit later on, I responded to another post where someone had suggested that we were “lucky” that it was only ransomware.
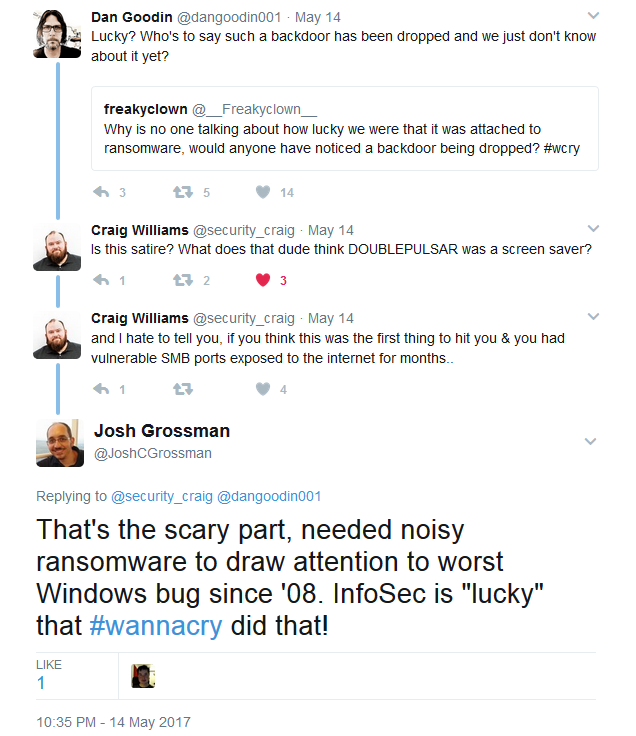
As I responded, the only thing that was “lucky” about this story was the fact that the WannaCry outbreak finally brought well-deserved attention to the incredibly dangerous exploits leaked by the TheShadowBrokers in April.
How bad is a vulnerability?
I blogged about these exploits on my employer’s blog, precisely because we wanted to make sure that the company’s clients had the relevant information to protect themselves. We don’t blog about every vulnerability or issue that comes to light but the unique danger posed by this leak meant that we decided it was important that we prepared advice. Like I said there, this probably the worst Windows vulnerability since 2008.
Given the overall panic, it seems that despite the leak of *working exploits*, MS17–010 was still not taken seriously enough by Microsoft or by the Industry. Microsoft in particular stuck to their guns and didn’t patch XP and 2003 for non-paying customers until it became prudent from a PR perspective.
We in the Information Security industry need to find a better way of communicating the risk posed by a security issue. The frustrating “branded vulnerabilities” trend has led to risk assessment based on logo quality rather than actual potential for damage.
The fact is that as noted in the 2016 DBIR (page 16), the most dangerous vulnerabilities are those for which real public exploits exist such as in Metasploit. TheShadowBroker’s release effectively met that criteria but despite this the outcry was less than something like Heartbleed or the damp squib which was Badlock.
Just patch it?

It is clear that there are plenty of organisations where patching is difficult or impossible. For organisations where it is difficult, security professionals need to help these organisations “choose their battles” where MS17-010 should have been a battle that was fought and won as soon as TheShadowBroker’s leak of live exploits was shown to be related to it.
However, for places where patching is impossible and to be honest in all mature organisations, the focus needs to shift to an “anticipate breach” posture whereby it is almost assumed that attackers will get in through unpatched vulnerabilities or just plain old phishing. In this model, the goal becomes preventing and detecting lateral movement through segmentation and better behavioural logging.
In Conclusion
So, in some ways maybe we got lucky that WannaCry drew so much attention to MS17–010 because it should now be easier to get buy-in to patch some of these specific flaws, just in time for the Metasploit module release (remember the DBIR metric above?)
However, despite this we must ask ourselves now, what other quiet malware was able to infiltrate Company networks whilst this flaw remained unpatched or unconsidered? We have already seen a couple of examples of this.
We need to be better at articulating risk regarding known issues but we also need the detective controls to be ready for the unknown issues as well.